Auth0
Auth0 is an identity and access management platform that provides authentication and authorization services for Guardian Connector deployments.
How Auth0 is used in Guardian Connector
Auth0 enables secure user authentication and access control across Guardian Connector tools:
- Single Sign-On (SSO) - Users authenticate once to access multiple Guardian Connector services
- User management - Centralized user registration, login, and profile management
- Role-based access control - Different permission levels for administrators and community members
Getting Started
- Create an Auth0 account at auth0.com
- Configure applications for each Guardian Connector service
- Set up user roles and permissions based on your community's needs
- Configure Auth0 credentials in your Guardian Connector environment variables
- Test SSO flow across your Guardian Connector tools
For detailed setup and configuration, see the Auth0 documentation.
User Approval Process
- User signs up for Guardian Connector applications (Superset, GC Scripts Hub,GC Explorer, etc.) using Auth0 — either by creating an account or using a service like Google or GitHub.
- Upon signup, the user will see a message like "Invalid login" on Superset, or "Your approval is pending" on GC Explorer, etc.
- An Auth0 tenant administrator approves the user by adding
"approved": trueto the user's App Metadata JSON. This can be found by navigating to User Management > Users, clicking on the user to approve, and scrolling down to the app_metadata section. - The user can now authenticate and log in to Guardian Connector applications.
Configuring an Auth0 Tenant
An Auth0 tenant is a dedicated instance of the Auth0 identity management platform that belongs to a specific organization or application. It acts as a container for all configurations, user data, and security settings related to your identity management needs. Each tenant operates independently, ensuring that the configurations and data within it are isolated from other tenants. This setup allows organizations to manage user authentication, authorization, and security policies centrally for their applications.
Follow these steps to set it up for your instance:
- In Settings, select "Production" as the Environment Tag.
- In Actions, set up a Flow for user approval.
- In Branding, make any customizations such as adding a logo and setting the background color.
- In Authentication / Database, ensure Sign Ups are enabled (they are by default).
- In Authentication / Social, enable
google-oauth2. Configure a Client ID and Client Secret for an OAuth 2.0 Client from a Google Cloud Platform project. See this section ongc-deployfor more information.
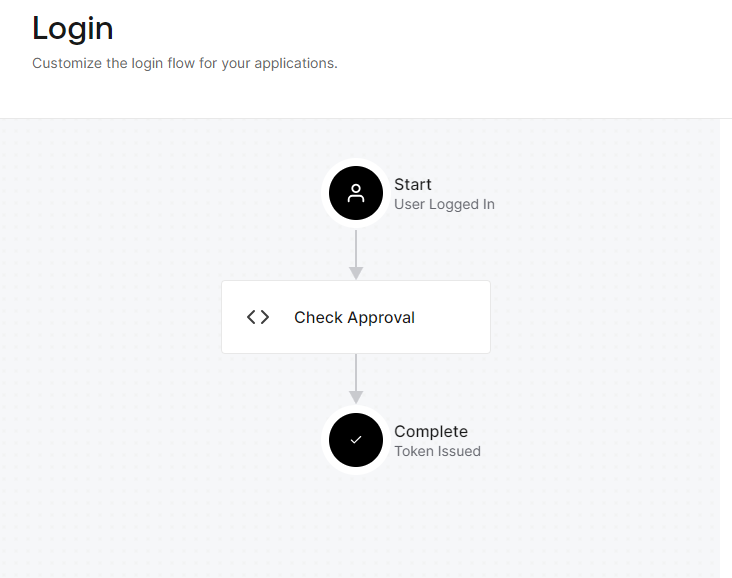
Creating an Auth0 Trigger Action for User Approval
To handle user approval in Auth0, a Trigger Action (named "Check Approval") serves as middleware between logging in and token issuance.
This is the code for that Action, based on the Common Use Cases in the Auth0 documentation:
exports.onExecutePostLogin = async (event, api) => {
// Check if the user is approved
if (event.user.app_metadata && event.user.app_metadata.approved) {
// User is approved, continue without action
} else {
api.access.deny('Your approval to access the app is pending.');
}
};
This Trigger Action should be added to the Post Login Flow on the Auth0 Actions -> Triggers page.
The Action checks if the boolean property user.app_metadata.approved is true and allows the user to proceed. Otherwise, it returns the message "Your approval to access the app is pending", which is also passed as a query parameter in the browser and used by applications like GC Explorer to indicate to the user that they need approval.